Tech
Refurbished IT Assets: Radical Tech Access for Agile, Forward-Thinking Businesses
In modern business needs, technology moves faster than most budgets, playing catch-up is costly. Owning every device isn’t just impractical—it traps capital, accelerates obsolescence, and adds hidden operational headaches. Smart Rental turns this paradigm on its head, offering professional-grade laptops, interactive boards, and IT devices through refurbished and flexible rentals. Here, technology isn’t a cost—it’s […]
How Leading Edge Protection Enhances Blade Longevity in Harsh Environments
The Challenge of Harsh Environments for Wind Turbine Blades Wind energy is one of the fastest-growing sources of renewable energy globally. However, the performance and longevity of wind turbines depend heavily on the durability of their blades. These blades are exposed to harsh environmental factors such as rain, hail, dust, UV radiation, and salt-laden air. […]
Emotional Accuracy and Intelligent Automation: Push Notification Advertising’s Future in E-Commerce
Emojis and conversational styles are used to emotionally connect with users, and the timing and tone of push notifications are carefully considered to optimise engagement. Discounts provided during user engagement have greater open and click-through rates, thus timing is also crucial. A key development in push notification ad is automation combined with contextual relevance, which […]
Productivity Apps, Intelligent Cloud Services, and World-Class Security in One Place – Microsoft 365
All of us need to deal with office work, but also require productivity apps and all kinds of different solutions. These apps are inherently useful for many different situations. That’s why it can be a very good idea to learn what apps you can use, how to use them and how you’re getting the best […]
A Network Upgrade – When Is The Right Time?
Businesses must plan to update their network equipment. It’s time to replace your hardware if it is slow, performs poorly, or frequently breaks down. Before buying expensive equipment, consider what the network needs to achieve. If you skip this step, you might need another upgrade in just a few years or even sooner. This article […]
How does privatenoter pioneer a new frontier in secure communication technology?
With the increasing prevalence of data breaches and cyber threats, individuals and organisations seek innovative solutions to protect sensitive information. Comes Privatenoter is a groundbreaking platform revolutionising how we approach secure communication. Privatenoter’s secure communication technology relies on end-to-end encryption as its foundation. This encryption method ensures that only the intended recipient accesses and reads […]
Elevate your tiktok game- Advantages of buying views
TikTok is a force to be reckoned with its short-form video format and captivating content, it has captured the attention of millions of users worldwide. However, in this highly competitive space, standing out from the crowd can be a daunting task. It is where the strategy of buying views comes into play. Faster growth and […]
Get visual with online whiteboard features for diagrams and mind maps
Online whiteboard tools provide virtual spaces where you create diagrams, flowcharts, mind maps, and more. With their versatile features, these tools allow you to visualize concepts, map out ideas, and bring visual clarity to your work. Visual thinking takes advantage of our brain’s innate ability to process visual information efficiently. Studies show that visuals are […]
All you need to know about Mechanism of Action (MOA)
Introduction Mechanism of Action (MOA) animations are a capable device utilized within the pharmaceutical and biotechnology businesses to outwardly clarify how a medication or an organic item works at the atomic or cellular level. These animations are significant for an assortment of groups of onlookers, including healthcare experts, patients, financial specialists, and understudies, giving a […]
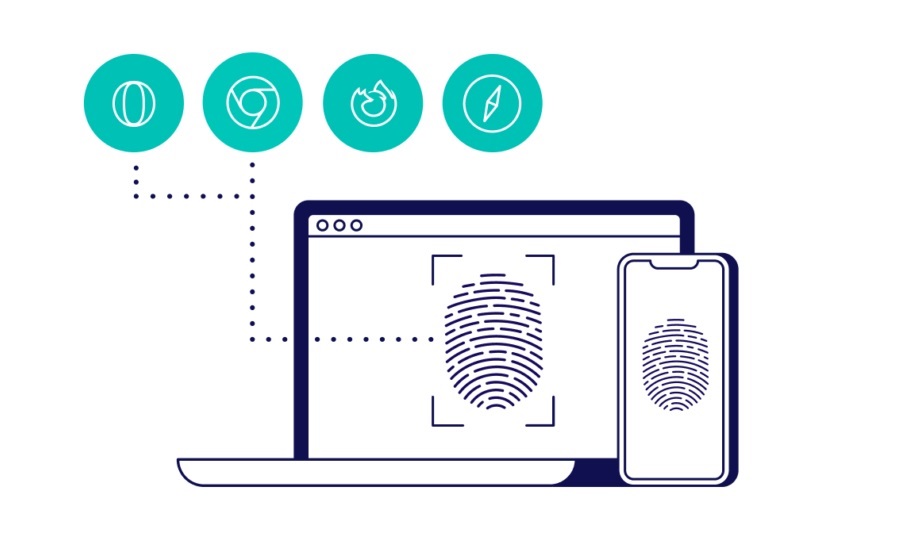
How Does Browser Fingerprinting Operate and What Is It?
Browser Fingerprinting: What Is It? Device fingerprinting is the silent evaluation of each web browser’s distinct configuration when it connects to a web domain. Of course, the fingerprint under examination consists of more than just the web browser; it also includes the operating system, installed languages, plugins, and the time zone set inside the browser, […]