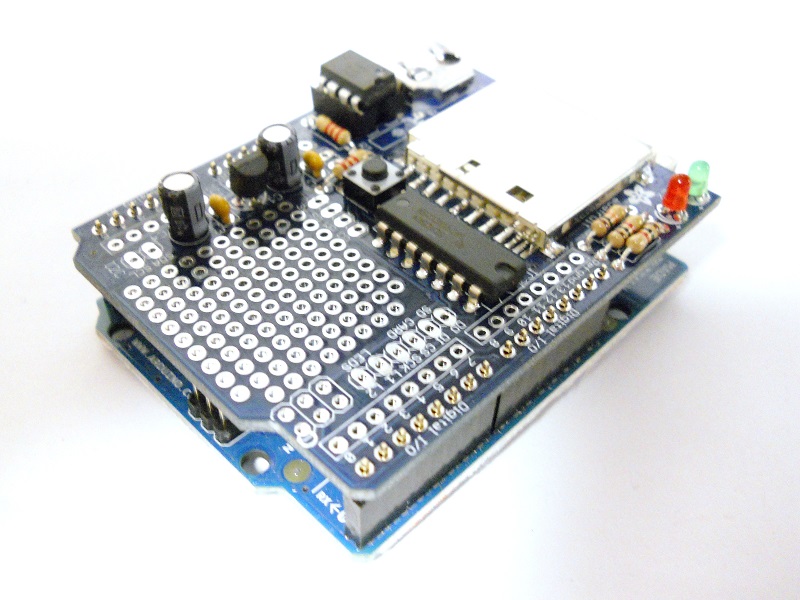
Hardware
The Return on investment of MICR Check Printing Versus Pre-Printed Checks
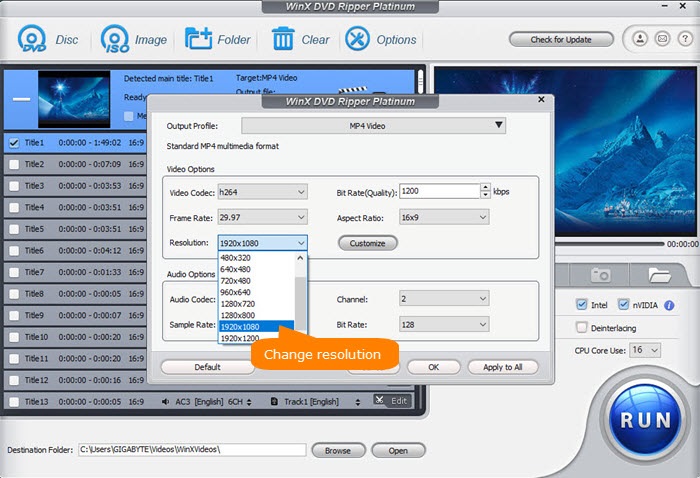
Software
Why Do You Need to Modernize Your RCM System?
Network Backup Software to cope with Data Proliferation
Technology
Get The Most Of The Advantages Of Uninterruptible Power Supply Systems
Hacking passwords being made easy
How Effective Could Be The Data Quality Management?
LATEST ARTICLES
Behind the Scenes – How SMM Panels Work and Why You Need Them
In today’s fast-paced digital world, social media is more than just a platform for sharing personal moments. It has evolved into a powerful marketing tool for businesses and influencers alike. Whether you're running a small business, managing a brand, or looking to boost your personal presence, social media is your gateway to a global audience. But with millions of users...
Amazon agencies – Balancing short-term wins and long-term growth
As the platform continues to evolve and competition intensifies, many brands turn to Amazon agencies for expertise in navigating this complex marketplace. Companies like these are crucial to helping businesses succeed on Amazon. Temptation of short-term wins The pressure to deliver immediate results is intense in the highly competitive Amazon marketplace. Both agencies and their clients often seek quick wins to...
A Network Upgrade – When Is The Right Time?
Businesses must plan to update their network equipment. It's time to replace your hardware if it is slow, performs poorly, or frequently breaks down. Before buying expensive equipment, consider what the network needs to achieve. If you skip this step, you might need another upgrade in just a few years or even sooner. This article discusses the key factors to consider...
How does privatenoter pioneer a new frontier in secure communication technology?
With the increasing prevalence of data breaches and cyber threats, individuals and organisations seek innovative solutions to protect sensitive information. Comes Privatenoter is a groundbreaking platform revolutionising how we approach secure communication. Privatenoter's secure communication technology relies on end-to-end encryption as its foundation. This encryption method ensures that only the intended recipient accesses and reads a message's contents. When you...
How to Build Your Own Country: The Engaging World of Political Simulation Games
In the digital age, the appetite for creating, managing, and leading virtual nations has surged, with political simulation games offering a unique blend of strategy, diplomacy, and governance. Among these games like NationStates, Politics and War distinguishes itself as a comprehensive platform where players step into the shoes of nation leaders, tasked with the monumental responsibility of guiding their...
Elevate your tiktok game- Advantages of buying views
TikTok is a force to be reckoned with its short-form video format and captivating content, it has captured the attention of millions of users worldwide. However, in this highly competitive space, standing out from the crowd can be a daunting task. It is where the strategy of buying views comes into play. Faster growth and momentum Building a substantial following on...
Get visual with online whiteboard features for diagrams and mind maps
Online whiteboard tools provide virtual spaces where you create diagrams, flowcharts, mind maps, and more. With their versatile features, these tools allow you to visualize concepts, map out ideas, and bring visual clarity to your work. Visual thinking takes advantage of our brain’s innate ability to process visual information efficiently. Studies show that visuals are processed 60,000 times faster...
All you need to know about Mechanism of Action (MOA)
Introduction Mechanism of Action (MOA) animations are a capable device utilized within the pharmaceutical and biotechnology businesses to outwardly clarify how a medication or an organic item works at the atomic or cellular level. These animations are significant for an assortment of groups of onlookers, including healthcare experts, patients, financial specialists, and understudies, giving a clear and locks way to get...
How Does Browser Fingerprinting Operate and What Is It?
Browser Fingerprinting: What Is It? Device fingerprinting is the silent evaluation of each web browser's distinct configuration when it connects to a web domain. Of course, the fingerprint under examination consists of more than just the web browser; it also includes the operating system, installed languages, plugins, and the time zone set inside the browser, among other things. When combined, these...
MFA vs. 2FA: What’s the Difference?
In today's digital age, safeguarding sensitive information and online accounts is of utmost importance. There is an ever-increasing need for robust security measures to protect individuals and businesses from cyber threats. Two widely known and utilized methods to enhance security are Multifactor Authentication (MFA) and Two-Factor Authentication (2FA). While these terms are often used interchangeably, it is important to...